Table of Contents
Building and deploying secure software is no longer an option–it’s a necessity. As software applications continue to increase in complexity and interconnectivity, they also pose greater security risks if not developed with care. This is where a Secure Software Development Lifecycle (SSDLC) comes in.
By taking a proactive approach and integrating security efforts throughout the entire development lifecycle, organizations can release better quality software to the market. This prevents security breaches, keeps data safe, and avoids loss of customer trust resulting from compromises after deployment.
This article will provide an overview of what an SSDLC entails, key differences from the traditional SDLC, the five main phases. It will also explore best practices, and how you can leverage expert guidance to implement a robust SSDLC.
What is Secure Software Development Lifecycle (SSDLC)?
Secure Software Development Lifecycle refers to the end-to-end set of processes and practices that integrate security across every phase of software design, development, testing, and deployment. It expands on the typical software development lifecycle (SDLC) by deliberately emphasizing security at each stage.
The goal of SSDLC is to methodically address potential vulnerabilities, weaknesses, and threats throughout the building, testing and release of your software application. This proactive approach results in software that is more secure, preventing data breaches, protecting privacy, and reducing business risk when deployed.
According to recent statistics, only 23% of companies state that their cybersecurity metrics are well understood at the senior executive and board levels. Additionally, over 29,000 identified common IT vulnerabilities and exposures (CVEs) have been identified globally. This demonstrates the need for security to be a priority throughout development workflows from inception to deployment of your software.
By adopting an SSDLC, your organization can release software to market with fewer security issues, lower risk, prevent loss of customer trust, and leakage of sensitive information. An SSDCL leads to securely engineered products that can withstand real-world attacks and avoid catastrophes after launch.
SSDLC focuses on security right from the start of your software development project. It measures and manages risk throughout the process, and results in resilient software that businesses can feel confident about despite a complex threat landscape. Prioritizing security initiatives saves time and money over patching vulnerabilities later on.
Key Differences Between SSDLC and SDLC (SSDLC vs SDLC)
Secure Software Development Lifecycle differs from the typical Software Development Lifecycle in the following key ways.
Focus on Security
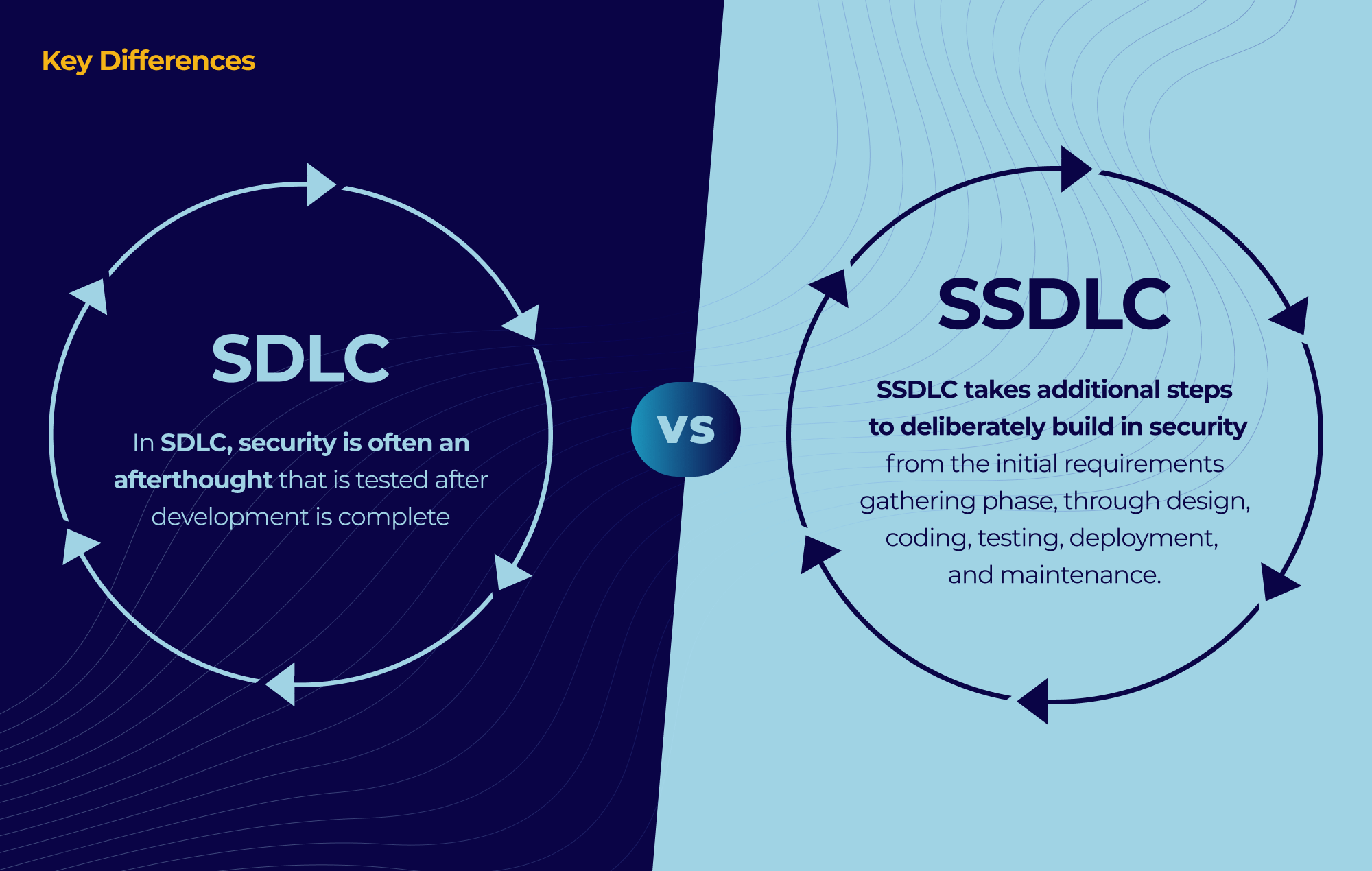
The fundamental difference between traditional SDLC and Secure SDLC is the emphasis on deeply integrating software security throughout the entire lifecycle. While typical SDLC focuses purely on meeting functional requirements, SSDLC places equal priority on proactively identifying, assessing and mitigating vulnerabilities at each phase.
In SDLC, security is often an afterthought that is tested after development is complete. In contrast, SSDLC takes additional steps to deliberately build in security from the initial requirements gathering phase, through design, coding, testing, deployment, and maintenance. Thisenables developers to remediate vulnerabilities early when they are easiest to address.
Additional security activities are conducted at every stage to uncover risks and establish protection measures proactively rather than reactively. Threat modeling, risk analysis, security architecture reviews, static analysis, dynamic analysis, and penetration testing all enable this.
Phases
The key phases of SDLC remain the same in SSDLC, but security considerations are implemented across each phase:
- Requirements: Detail the security features required, conduct abuse cases, and undertake threat modeling.
- Design: Define secure architecture, protocols, key management, and access controls.
- Implementation/Coding: Adhere to secure coding standards, sanitizing inputs/outputs.
- Testing: Perform security testing such as penetration tests, static analysis, and code reviews.
- Deployment: Carry out final security reviews and establish monitoring protocols.
- Maintenance: Manage patches and updates to fix vulnerabilities.
Tools and Practices
SSDLC utilizes various tools and practices specifically focusing on security analysis to uncover vulnerabilities proactively. These include:
- Static Application Security Testing (SAST): Analyzes source code for security flaws without executing programs. This test checks for injection flaws, buffer overflows, cross-site, and scripting issues.
- Dynamic Application Security Testing (DAST): Tests applications while in runtime to detect vulnerabilities that only surface during execution, as well as analyze attack surface.
- Software Composition Analysis: Scans third-party open-source libraries/components used to highlight vulnerable dependencies early.
- Penetration Testing: Simulates cyber attacks to evaluate real-world readiness and uncover overlooked gaps in software defenses.
- Threat Modeling: Models various attack scenarios and adversary profiles to define security requirements and priorities.
These techniques are executed continuously throughout your software development lifecycle via automation to embed security, instead of just running them once prior to launch. These tools integrate with continuous integration and continuous delivery pipelines changing the cultural standpoint on security.
Organizational Culture
A key difference between SDLC and SSDLC is the organizational culture and mindset towards security.
In a typical SDLC, security is often treated as an afterthought or impediment to releasing your software. It is seen as a cost center rather than enhancing the quality of your software. Developers and managers try to circumvent security processes rather than embracing them.
Conversely, SSDLC requires the integration of security as an organizational priority and shared responsibility between developers, architects, product owners, QA, security teams, and executives. Security needs to become ingrained in the organizational culture.
Rather than treating security as a bottleneck, SSDLC frames it as an essential practice for engineers. Security awareness becomes ingrained through training, support channels, and leading by example. There is a cultural shift on security away from it being regarded as simply a compliance checklist item. This cultural transformation is essential for organizations to truly reap SSDLC benefits.
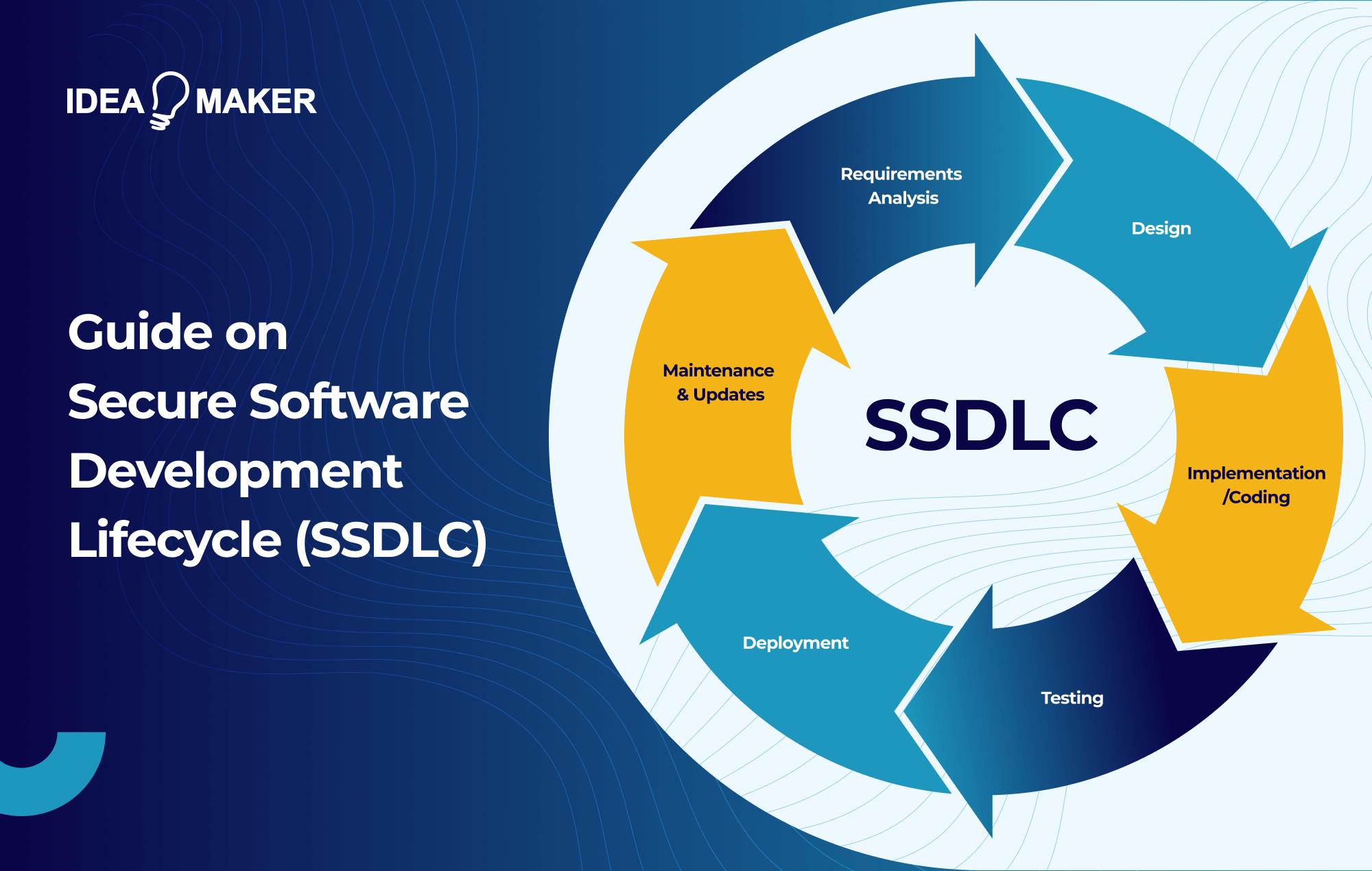
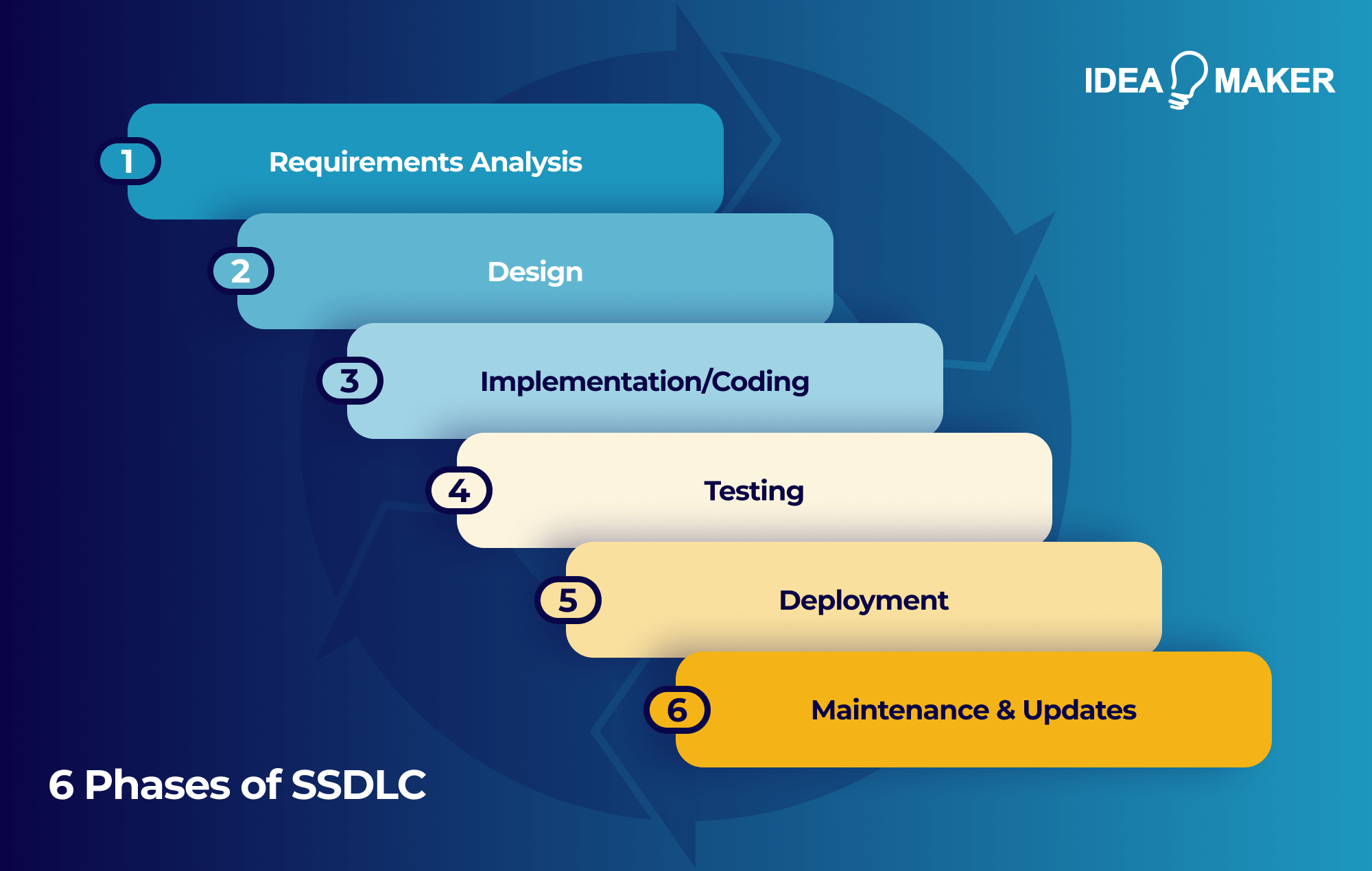
6 Phases of SSDLC
Let’s walk through the five phases of SSDLC so you and your team can effectively implement them into your processes.
-
Requirements Analysis
The requirements gathering phase focuses on defining both functional and security requirements hand-in-hand. This includes identifying use cases, data flows, trusted boundaries, integrating security controls, and detailing cybersecurity-related features to be built into your software based on risk appetite.
Formal threat modeling is conducted using methods such as STRIDE, PASTA, or VAST to understand risk scenarios and establish vulnerability priorities. Potential attackers and their goals are outlined to define abuse cases with requirements analysis setting the foundation for secure software.
-
Design
The design phase focuses on defining your software architecture, components, and data flows securely from the outset rather than just to meet functional requirements. Security is made a key priority in initial design discussions and blueprints. Some examples of secure design best practices adopted early on are:
- Minimizing access and privileges to reduce risk: Only allow database access or features needed rather than full access.
- Validating and sanitizing inputs: Check for malicious inputs like SQL injection attempts during data entry.
- Encrypting sensitive data: Protect any personal or financial data stored or transmitted.
- Logging user activities: Record admin actions, logins, and data access to identify suspicious behaviors.
The goal is to deliberately design your software to proactively avoid introducing security gaps from the outset of your software development project. This approach is not about just meeting functional requirements or adding security as an afterthought. Rather, it is about making security everyone’s responsibility, from your initial architecture planning throughout your development to deployment.
-
Implementation/Coding
Granular secure coding guidelines are established using robust standards. Static analysis and dynamic analysis tools are seamlessly integrated within continuous integration and continuous delivery pipelines to accurately identify vulnerabilities and bugs as developers write code. Mandatory code reviews also examine common vulnerability patterns that tools can miss.
-
Testing
Rigorous security testing is undertaken, not just functional validation. This includes:
- Penetration Testing: Simulating cyber attacks to evaluate real-world readiness and uncover gaps early.
- Malware Analysis: Detects backdoors, logic bombs, or other malicious code inserted via tools such as static analysis.
- Attack Surface Review: Analyze the entire application landscape for risky endpoints vulnerable to attackers.
- Negative Testing: Intentionally fail or break system components to identify critical flaws.
Detailed security test cases are created to validate authentication, access controls, encryption, and other countermeasures. The goal is to uncover oversights early when they are cheaper to fix.
-
Deployment
As software transitions from staging environments to final production release, a comprehensive vulnerability assessment and penetration testing exercise is conducted to uncover security gaps that may have emerged during integration with other systems.
Your goal here is to catch high severity flaws prior to real-world exposure. Once your application is live, robust threat monitoring and analysis capabilities must be in place to continually evaluate risks. Your security team should scrutinize user traffic, data flows, access logs, and activities to detect anomalies indicating potential attacks or breaches before they escalate.
For example, if a user account starts accessing databases they don’t normally use at odd hours, it merits investigation. Your production environment needs rigorous monitoring because that’s where adversaries focus their efforts to exploit vulnerabilities in an attempt to cause real damage. Hardening security before and after you release your software via testing and threat hunting is critical for SSDLC.
-
Maintenance & Updates
Your work doesn’t end once your software is released. SSDLC mandates regular patching of vulnerabilities in your application code and third-party dependencies. Rather than just fixing bugs, updates take a proactive approach to improving security.
For example, updates:
- Address newly discovered vulnerabilities based on threat intel
- Improve encryption, access controls, and logging as per new attack trends
- Refine secure coding standards to close loopholes
- Evaluate new security tools to bolster defenses
Your goal is to constantly adapt and upgrade security measures before threats escalate. Quickly patching critical issues without downtime is essential.
Undertaking rigorous security reviews across your entire SSDLC results in robust software that avoids data leakage, security gaps, and loss of customer trust once deployed. However, your maintenance phase sustains these outcomes by continuously assessing emergent risks rapidly improving defenses rather than remaining static after launch.
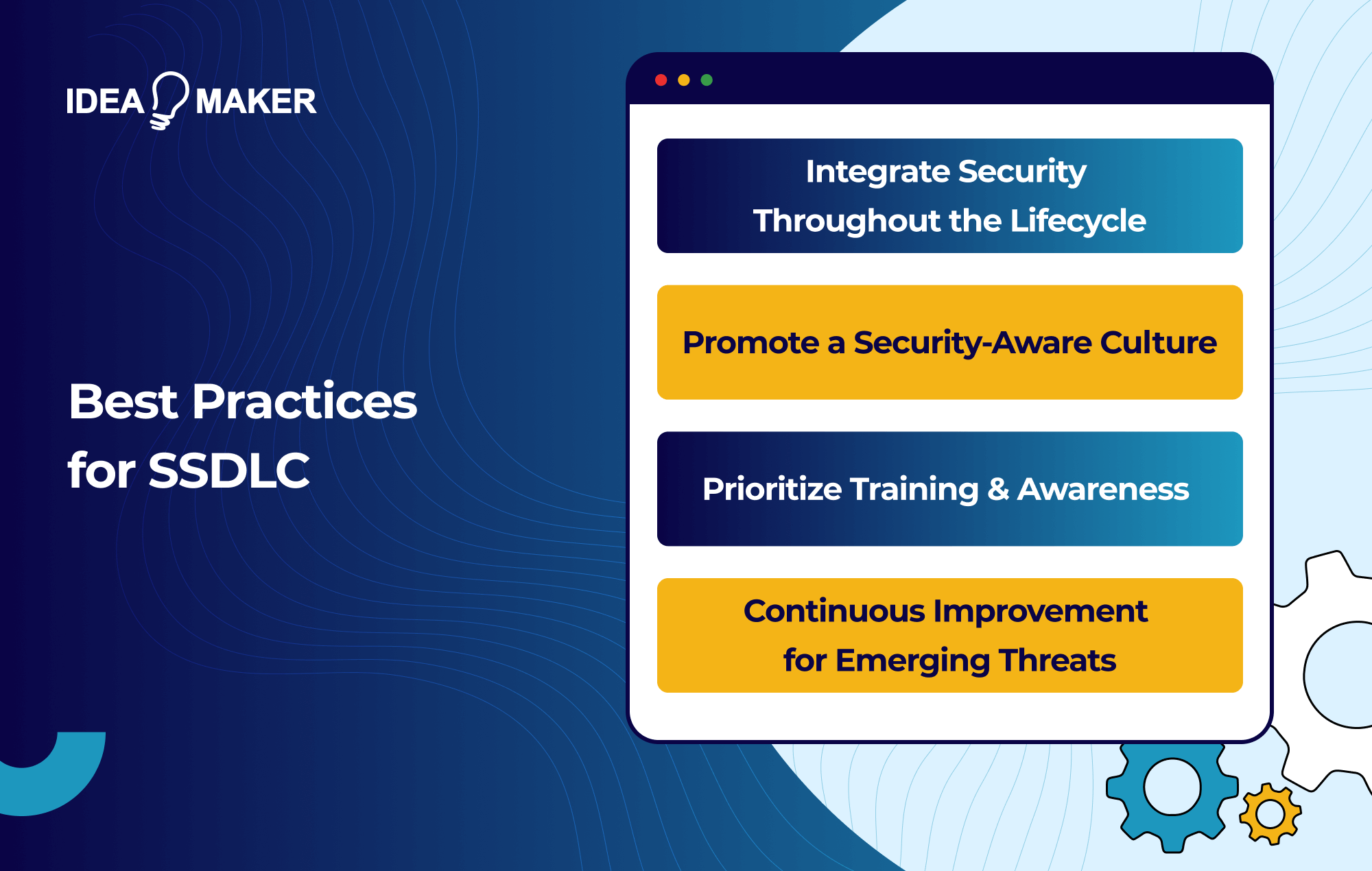
Best Practices for SSDLC
Implementing SSDLC requires adhering to proven security best practices across analysis, design, coding, testing, and deployment. Simply going through the motions of an SSDLC without sound, secure software engineering principles is ineffective. These are some best practices for implementing a secure software development lifecycle:
Integrate Security Throughout the Lifecycle
Integrate security into your entire development lifecycle–from initial requirements gathering to design, coding, testing, and deployment stages–instead of just retrofitting it or focusing on bugs/vulnerabilities later. You should make it an equal priority to functional goals in analysis, planning, development, and post-deployment activities.
You should conduct threat modeling early on, continuing to evolve it across phases to uncover overlooked risks proactively based on known attack patterns and adversaries.
At the same time, you should integrate security-focused code reviews, static analysis, dynamic analysis, and penetration testing tools directly into continuous integration and continuous delivery pipelines. This will enable you to rectify vulnerabilities early in your development process when it is cheaper and therefore is more cost effective.
Promote a Security-Aware Culture
Transitioning to an SSDLC is not just about process changes. The most vital aspect is fostering an organizational culture that ingrains security across your teams. This ranges from developers and architects writing your code to your quality assurance team testing it, information security team, and business leadership team overseeing direction.
Everyone must be aligned in viewing security as a shared priority and responsibility, rather than an afterthought. The outcome of this is a cultural shift from the top-down and bottom-up. Leadership must invest, budget, provide tools, tie security to executive metrics, and participate in assessments. Grassroots developer-led initiatives around secure coding practices need nurturing.
By breaking down barriers between functional silos, information security teams can enable developers via mentoring and platforms for collaboration rather than dictating policies. App teams must welcome security guidance proactively. This collective transition is vital as the success of your SSDLC relies on people putting principles into practice. Culture and mindset transformation enables changes to technical processes.
Prioritize Training & Awareness
You should conduct regular secure software development training sessions, workshops, and mock audits to educate all personnel on the latest application risks, tools, coding best practices, and remediation guidance.
You should ensure that everyone is aware of organizational policies, compliance requirements (PCI, DSS, and HIPAA), and incident response procedures and can access actionable resources to build their skills. Focused training helps to ingrain secure coding habits while empowering teams to own security rather than view it as a bottleneck. Prioritizing continual education is instrumental to achieving SSDLC’s success.
Continuous Improvement for Emerging Threats
The cyber threat landscape evolves rapidly, with attackers constantly innovating new attack vectors. Conversely, business conditions, compliance rules, and technologies also undergo frequent changes. Your SSDLC must adapt security practices accordingly through continuous assessments and upgrades.
You should take a proactive and dynamic mindset to security. Rather than conducting periodic audits, threat models, tools and processes which all require real-time upgrading you should learn from past security incidents, escapes, and attacks. This will enable you to uncover control gaps then analyze post-mortems which will enable you to derive critical insights that can bolster SSDLC.
You should undertake quick iterative sprints to improve security capabilities. For instance, integrating new tools into continuous integration and continuous delivery pipelines based on updated adversary tactics. Your goal is to iterate and upgrade SSDLC components on an ongoing basis so that security processes and practices continuously improve, rather than remain stagnant. This ensures readiness against emerging threats and zero-day attacks.
Integrating security efforts at all levels of your organization, promoting awareness, ensuring training, and continuously improving development practices will enable a robust SSDLC implementation. This will have the long term effect of building resilience into your software application.
An effective SSDLC is not a one-off activity but rather an evolving program that develops code with greater security, and prevents additional security incidents in the future.
Let Idea Maker Help You With a SSDLC
Developing secure software is critical in today’s interconnected world. Idea Maker understands the challenges organizations face in adopting a robust yet efficient Secure SDLC. With years of experience in secure engineering and assurance programming, our experts can guide you through integrating security across analysis, planning, design, coding, testing, and ongoing updates.
At Idea Maker, we can offer a comprehensive range of services to enhance your SSDLC. We help define security requirements, conduct threat modeling, establish policies and guidelines, implement analysis tools, strengthen testing practices, and train personnel through our proven processes.
Whether you need an assessment to understand gaps in your current SDLC, want to implement an SSDLC from scratch, or improve an existing one, Idea Maker can provide a solution tailored to your needs.Contact us today for an in-depth discussion on how Idea Maker can enable your next generation Secure Software Development Lifecycle program.